~ Hacks on smart technologies expected in 2016 could result in serious and fatal damages
~ Mobile devices continued being hotbeds for cybercriminals looking to exploit security flaws
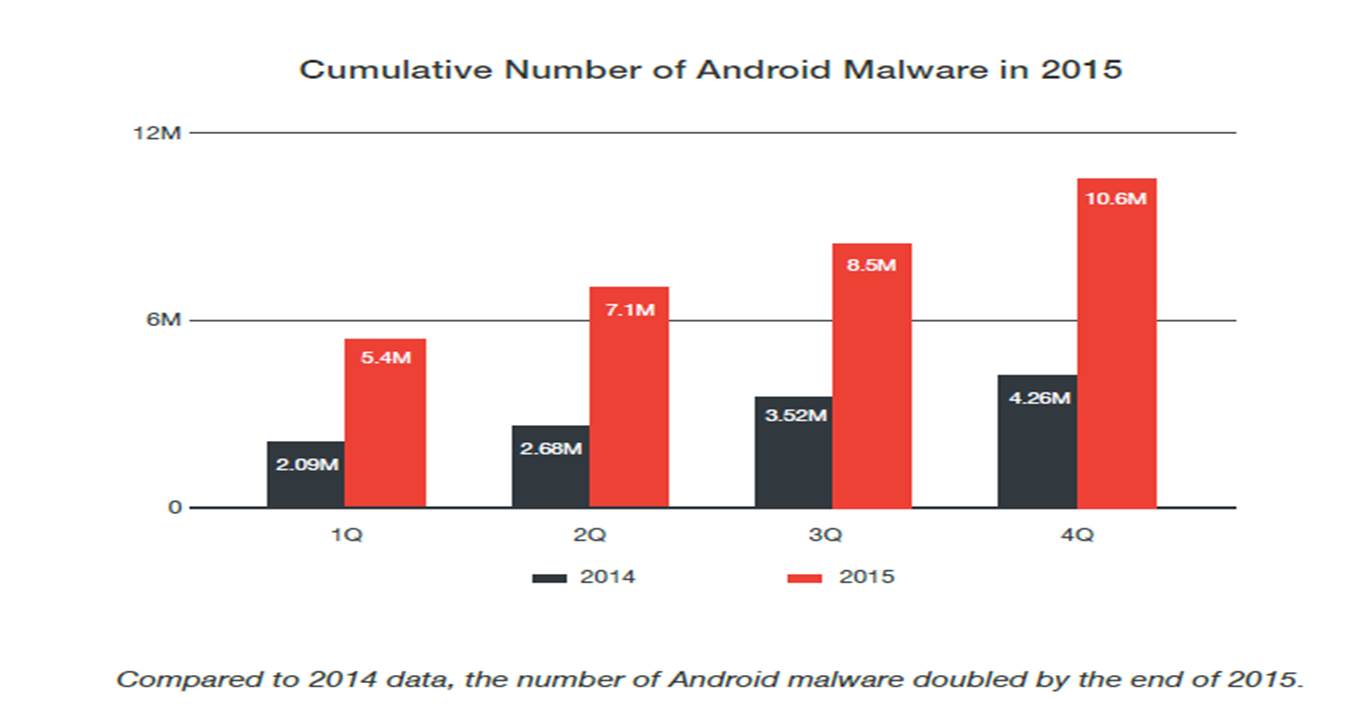
The Android security is becoming a serious concern as the Android Malware was reported to by double in 2015 as  compared to 2014. Trend Micro Incorporated released its annual security roundup report which dissects the most significant security incidents from 2015. One of the top activities noted included the rise in Android Malware and impact also included the aggressive adoption of smart technologies.
compared to 2014. Trend Micro Incorporated released its annual security roundup report which dissects the most significant security incidents from 2015. One of the top activities noted included the rise in Android Malware and impact also included the aggressive adoption of smart technologies.
Android’s MediaServer component took a lot of hits in 2015. Vulnerabilities found in the component can be exploited to perform attacks using arbitrary code execution. Such attacks could force a device’s system to go on endless reboot, draining its battery. It can also be used to render Android devices silent and unable to make calls due to unresponsive screens. Vulnerability in Android’s manifest file may also cause devices to experience constant rebooting, making the device totally useless.
Some other Android vulnerability include the Android debugger Debuggered vulnerability we discovered in June. It can be utilized to expose a device’s memory content. The Android Installer Hijacking vulnerability, meanwhile, gives hackers the ability to replace legitimate apps with malicious versions in order to steal information from the user.
The Samsung SwiftKey Keyboard vulnerability (CVE-2015-4640 and CVE-2015-464124) had a pre-loaded malicious code masquerading as additional language packs that put over 600 million Samsung Galaxy series phones at risk. We also uncovered the Apache Cordova25 mobile API framework flaw, which remotely exploits applications with a mere click of a URL.
Although the state of Apple security is relatively better than of Android’s, Apple’s trusted walled garden also took some hits in 2015. The emergence of vulnerabilities like iOS Quicksand and AirDrop proved that iOS users could potentially be hit with exploits. The malicious code XcodeGhost26, while technically not a vulnerability, was also able to affect several users in China and the US.
2016 Outlook
One of the challenges we noted in our 2016 security predictions is the likelihood of more hacks on smart technologies that could result to serious and even fatal damages. These incidents serve as proofs of concept, solidifying what we previously thought was only possible in fiction. The need for security and testing of IoT devices is much stronger now, and manufacturers are expected to step up to the plate to protect their customers’ privacy and physical safety.
These Internet-connected devices can still be avenues to data loss and compromise. Most of these devices were designed with functionality in mind; security, only secondary. In order to keep these devices protected from attacks, developers need to be able to push regular updates and patches to close off any holes attackers can exploit. This problem is synonymous to when Android devices were first introduced to the workplace. The same fragmentation issue Android continues to experience plagues IoT as well. Since these devices do not run using a single OS—such as the case of Android—it complicates the updating process and leaves large windows open for compromise. While there are no current solutions designed to protect IoT, enterprises need to start building their security posture around these potential liabilities.