Fake Support Scam Calls requesting to remove computer errors caused by Viruses, they link through call centre to crack system.
ESET, global provider of security solutions for businesses and consumers, warns against the cold call support scams which have been growing increasingly. These calls sound like extending their services to resolve the problems on ones system and end up fracturing the system. Through cold calling and addressing themselves as representatives of well-known companies, they try to convince the customers that they have detected viruses or other malware on their system and they would like to remotely access their systems to solve the problem.
Scammers will give a call to any well-known company in the heavy Indian accent (Yes, our research shows few of them from Kolkata, all over the world) asking for paid support so that they can access the companies details through team viewer or any such software.
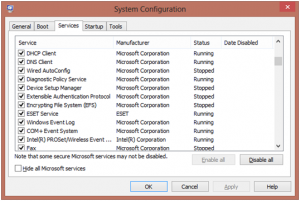
Much of these processes will be found out by Event Viewer and Prefetch that there are problems on customers Windows PC that need addressing. Scammers are also using a new trick along the same lines, but not seen used before, using the system utility MSCONFIG. The following graphic shows the sort of result that can be seen under the services tab.
Here, each service shown as ‘Stopped’ in the Status column is symptomatic of a system problem or of malware. In fact, while the System Configuration utility can certainly be used to help with troubleshooting, the fact that a service is shown as ‘Stopped’ simply means that it isn’t running. It certainly doesn’t prove the existence of a problem. Different utility, same kind of misrepresentation.
Support call is legal
Scammers also attempt to combine the use of unequivocal malware (a program that combines fake AV functionality with a basic screen locking capability) with support scamming, by driving the victim to contact a ‘helpline’. Once the victim makes the call, the con is much the same as in the cold-calling scams, but now the scammer can say that the victim called asking for the service, thus sidestepping legal countermeasures based on legislation that proscribes unsolicited cold-calling. Whether this lateral arabesque would stand up to close judicial scrutiny remains to be seen, but it’s clear that someone is putting some serious effort into prolonging the scam’s lifecycle.
In few cases of call centre scam, the spammer log into your PC and install Microsoft Office using a keygen to sidestep Microsoft’s licensing process, but it does suggest both, an alternative support (black) market and an alternative solicitation approach – “Itman Kool2” looks for customers using SMS spam and a Yahoo mail account. It’s consistent with the new ‘you called us, we didn’t call you’ approach, and it’s consistent with the common support scammer practice of charging for installing an evaluation version of security software, having a possible connection with scams.