Followed by consumers with 27% and Enterprises with 19%.
Malware attacks in Point-of-Sale has been there for a 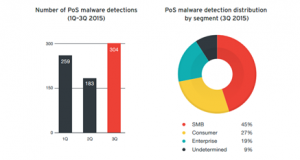 while but most interesting is that cybercriminals have shifted from using targeted-attacking format to traditional mass-infection tools like spam, botnets, and exploit kits.
while but most interesting is that cybercriminals have shifted from using targeted-attacking format to traditional mass-infection tools like spam, botnets, and exploit kits.
According to TrendLabs, attackers went after as many vulnerable PoS devices as possible in hopes of hitting the jackpot. They relied on tried-and-tested tactics like spamming as well as tools like macro malware, exploit kits, and botnets. They must have done something right because the PoS malware detection volume grew 66% Q1-Q3. SMBs, which had poorer protections in place compared with large enterprises, suffered most.
SMBs proved lucrative and easy point-of-sale (PoS) malware attack targets this quarter. This could be due to the extensive customer databases they keep with minimal to nonexistent security. We’ll likely see more of such attacks in the future. The slow adoption of next-generation payment technologies like the Europay, MasterCard, and Visa (EMV) and contactless Radio-Frequency-Identification (RFID)- enabled credit cards, mobile wallets (Apple Pay®and Android Pay™), and new payment-processing architectures could also adversely affect the security landscape.
A PoS random access memory (RAM) scraper made its way into devices aided by the Angler Exploit Kit, which is known for using malvertisements and compromised sites as infection vector.
Kasidet or Neutrino malware began sporting PoS-RAM-scraping capabilities this quarter. Kasidet, a commercially available builder, is known for its use in DDoS attacks, hits into PoS systems via malware-laced spam. As a result, its latest iteration accounted for 12% of this quarter’s total PoS malware detection volume.






