If you still haven’t decided how you plan to pay your bills while you’re in Brazil – cash or credit card– it is high time to do so. Kaspersky Lab warns that Brazil has some of the most creative and active criminals specializing in credit card cloning. And, unfortunately, they love to target foreigners who don’t know how to protect their cards when withdrawing money from an ATM or paying for their drinks in a restaurant. But our experts have some useful tips to protect against the most common attacks on ATMs and point of sales (PoS) devices in Brazil.
Avoiding credit card cloning
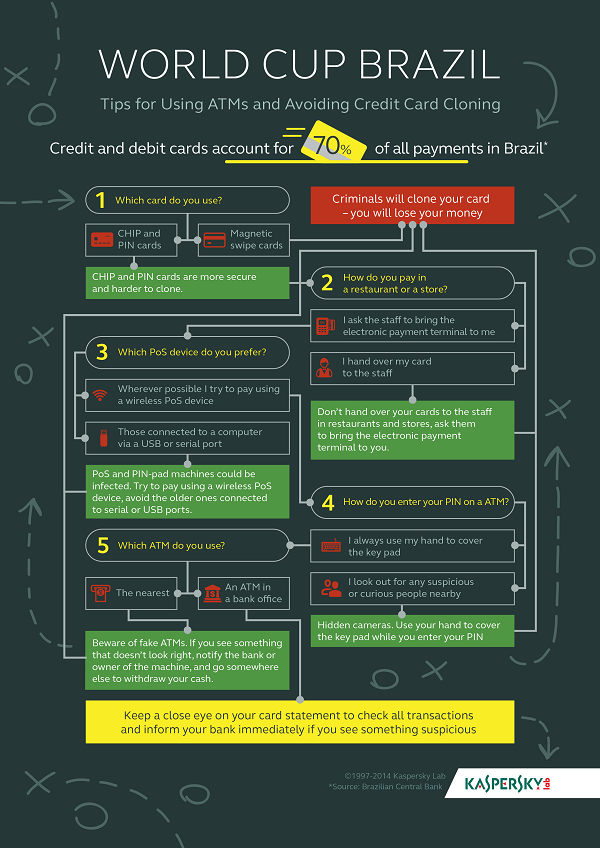
PoS devices are very common in Brazil – according to the Brazilian Central Bank, credit and debit cards account for 70% of all payments in the country. Chip-and-PIN cards are accepted by almost all businesses, even by cab drivers.
• Tips: despite some recent news about security flaws in this protocol, chip-and-PIN cards are still more secure and harder to clone than magnetic swipe cards. If you don’t already have this type of card, ask your bank if it’s possible to get one before you travel.
In Europe and North America, many people are in the habit of handing over their cards to staff in restaurants and stores. In Brazil, this can be dangerous.
• Tips: please don’t do this – you’re presenting fraudsters with a golden opportunity to clone the card, and the temptation is inevitably too strong to resist. Ask the staff to bring the electronic payment terminal to you.
• Be careful of chance encounters or accidents which might take your card out of reach for a moment. If it happens, check that the card you get back is really yours. If you have any doubts, report it immediately to the bank.
PoS and PIN-pad malware
So-called Chupa Cabra malware and Trojan-Spy.Win32.SPSniffer, a malware family with several variants developed in Brazil and seen in the wild since 2010, affects PoS and PIN-pad devices, both of which are very common in the country. These devices are connected to a computer via a USB or serial port to communicate with electronic funds transfer (EFT) software. The Trojan infects the computer and sniffs the data transmitted through these ports.
The PIN is encrypted as soon as it is entered, most commonly using triple DES encryption. But Track 1 data (credit card number, expiration date, service code and CVV) and the public chip data aren’t encrypted in the hardware of old and outdated devices. These are sent in plain text to the PC via USB or serial ports. Capturing this data is enough to clone a credit card.
• Please keep a close eye on your credit card statement to check all transactions and inform your bank immediately if you see something suspicious.
• Wherever possible try to pay using a wireless PoS device – they are a bit more secure than the older ones connected to serial or USB ports.
Using ATMs in Brazil
Brazil has 118 ATMs per 100,000 adults according to the World Bank, placing it ninth in the world in terms of ATM numbers. This presents lots of opportunities for fraudsters to install skimmers, also known as “Chupa Cabra” devices.
• Tips: use your hand to cover the key pad while you enter your PIN, it is a great way to foil most skimmers, which tend to rely on hidden cameras.
• If you see something that doesn’t look right, notify the bank or owner of the machine, and go somewhere else to withdraw your cash.
“Be cautious while using ATMs or paying with your credit card. Don’t forget that cybercriminals in Brazil perform their malicious schemes all the time. Even during the day you can see them hanging out, wearing flip-flops and beachwear while installing skimmers in a crowded bank. Also remember that it’s far more secure if your transactions happen right in front of you. Be careful of chance encounters or accidents which might take your card out of reach for a moment. If that happens, check that the card you get back is really yours. If you have any doubts, immediately report the incident to the bank,” said Fabio Assolini, Senior Security Researcher with Kaspersky Lab’s Global Research &Analysis Team.
More information can be found at securelist.com.